In a recent post, I highlighted the threat of a recent phone scam involving the HMRC, in this blog post I’ll give you more of a breakdown of phishing, vishing and smishing and give you some examples of how cyber criminals will try to fool you in attempts to gain your details.
phishing
Similar to the art of fishing which is defined as ‘the activity of catching fish, either for food or sport’, phishing is the cyber equivalent where criminals actively try to ‘catch’ your personal information by using deceptive social engineering techniques in the hopes of gaining access to your accounts both personal and financial.
Phishing is carried out via email to obtain sensitive information or data. This is done by spoofing (faking) the email to look like it’s come from a trusted source but with subtle differences. These emails are designed in a way to make you click a malicious link which would take you to a fake website created by the criminals in the hopes that you enter personal information or allow the criminals to install malware (malicious software which could freeze your system or lock your files as part of a ransomware attack).
How does phishing work?
The two main methods criminals use in phishing attacks are links to malicious websites and including malicious attachments. Usually, malicious links will take you to cloned websites of ones you are very familiar with and the malicious attachments usually have ‘click bait’ names such as ‘INVOICE’ which then install malware on your device when opened.
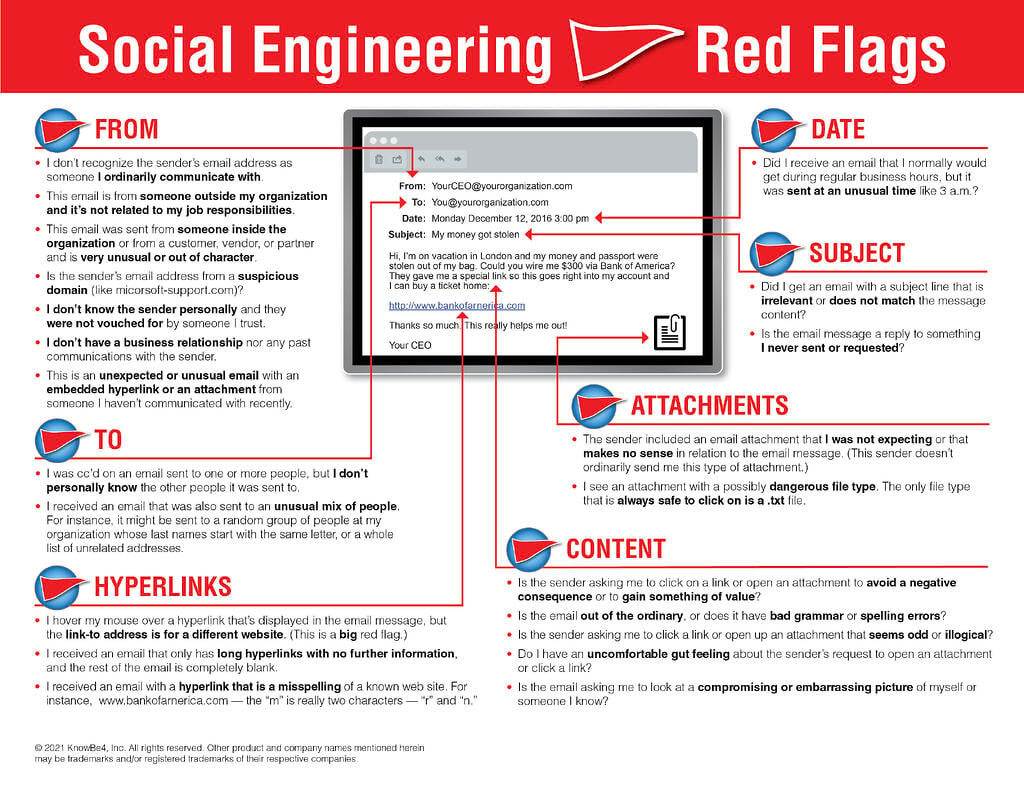
Below is a picture I have taken from the brilliant http://phishing.org which highlights some red flags if you think you have received a phishing email. I have also attached a couple of examples so you know what to look out for.
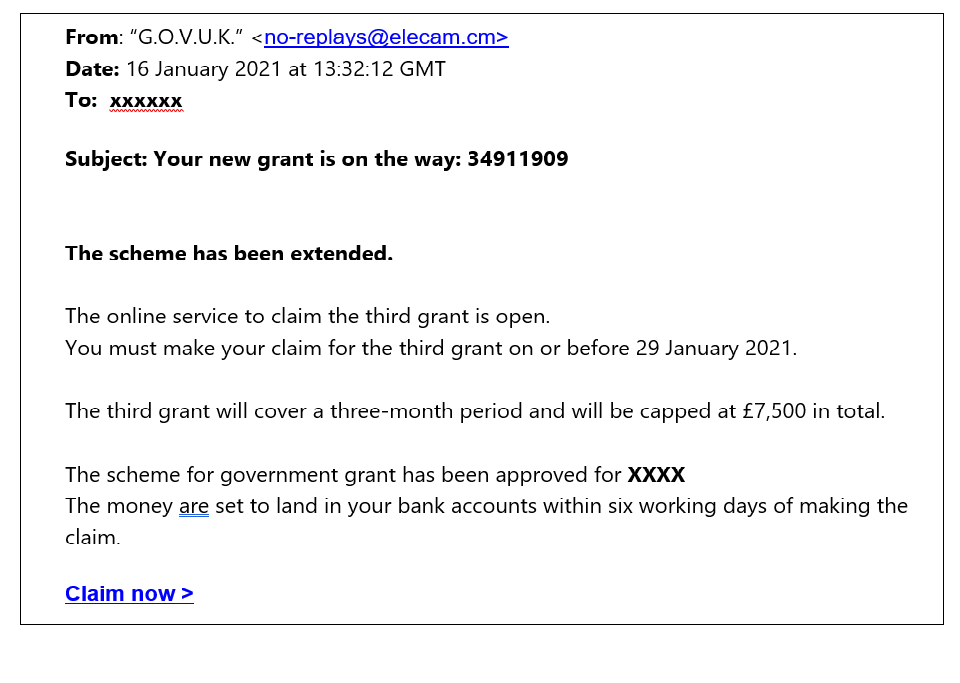
COVID19 GRANT PHISHING EMAIL
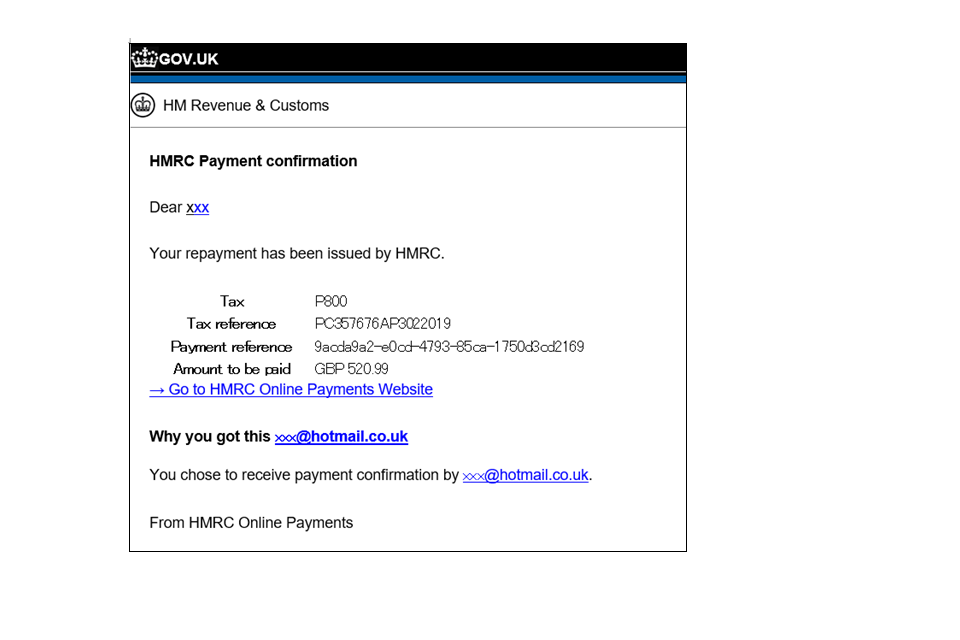
scam email with link to phishing website
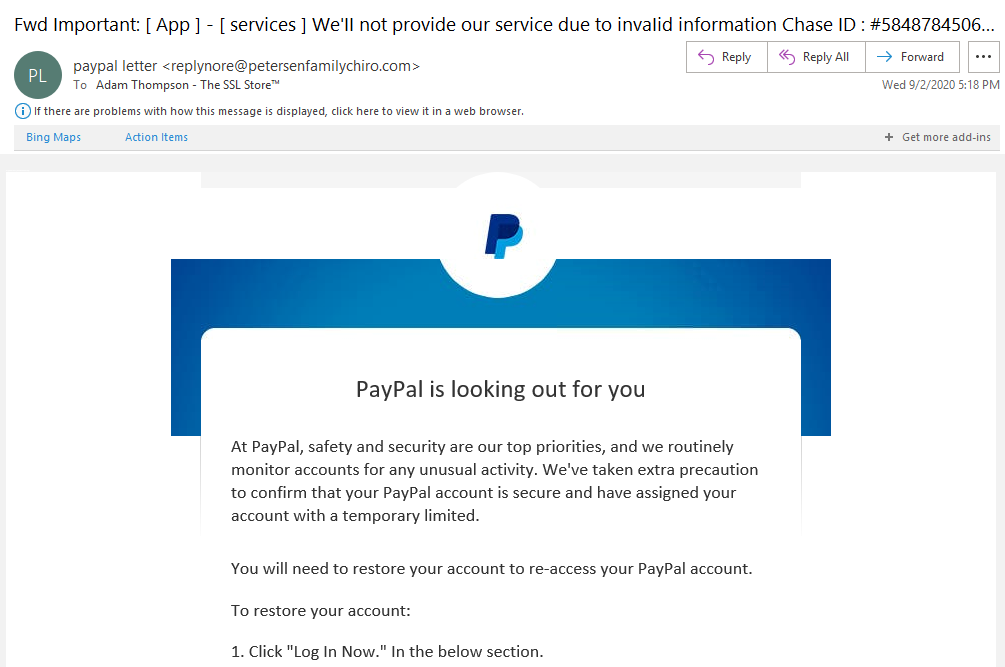
paypal phishing email
4 things to look out for
- Legitimate companies will usually address you by name.
- Legitimate companies will not ask for your sensitive personal information over email.
- Phishing emails are riddled with spelling mistakes.
- Hover your mouse over any link to see the destination of the URL.
VISHING + SMISHING
Vishing and smishing have the exact same concept of phishing but are just two specific ways in which criminals will try to steal your information.
Vishing is the fraudulent attack of making phone calls or leaving voice messages in the attempt to get victims to reveal personal information such as bank details and credit card numbers. During a vishing call, criminals will use social engineering techniques to get you to trust them and believe they are who they say they are. They will often spoof their phone number, so it looks like it’s coming from the official business it’s pretending to be. The most common vishing scam is vishing banking. These scams involve a call from someone who says they’re from your bank and that there is problem with your account or with a payment, they will then ask you to transfer funds to a different account to fix the problem. One of the most recent vishing scams is the HMRC tax fraud scam which I wrote about in my last post.
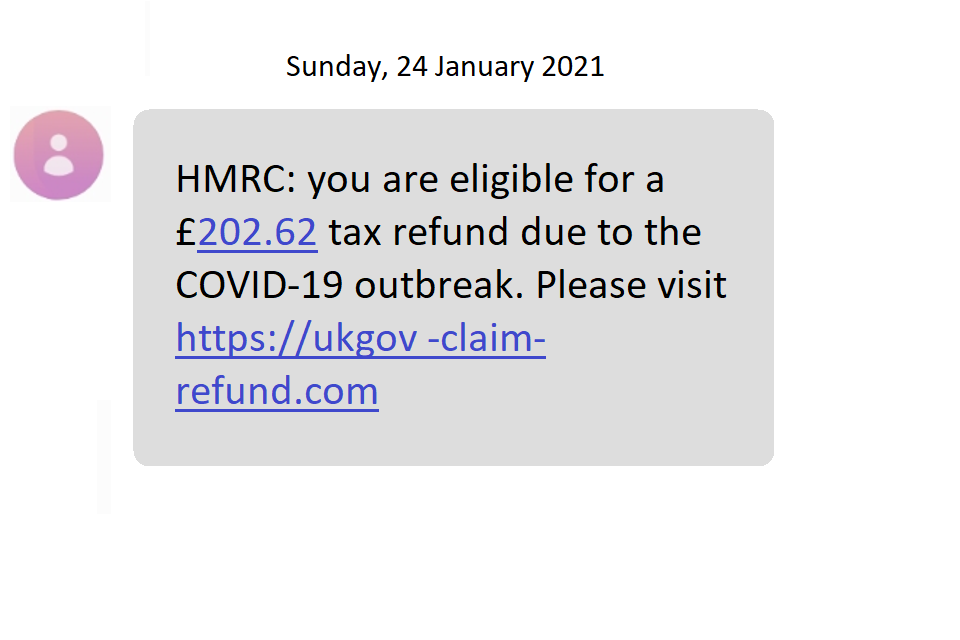
Smishing is the fraudulent attack that uses misleading text messages to trick victims into giving your private information via a text. Smishing is the same scam as phishing and vishing but the criminals just use text messages in the hopes that you’ll trust this form of communication more. These text messages again may include links which will take you to cloned webpages asking you to input usernames, passwords, and credit card details.
Below are a few examples of smishing attempts.


Final thoughts
Since the start of the coronavirus pandemic more and more of us have been victims of phishing attacks. This is due to criminals taking advantage of our new work from home lifestyle, we are more susceptible to these scams as we are making more calls than before, reading more emails, and generally communicating digitally a lot more than if we were still working in the office. Unfortunately, pandemic or not, criminals will take advantage of their victims in any way they can to benefit financially. Hopefully, this blog post has highlighted some of the things to look out for and will hopefully make you think twice before you click on that email from Amazon with your £1000 gift card (insert side eye emoji here). There are so many incredible resources just a google click away when it comes to phishing scams, many large businesses are aware of them and have their teams dedicated to dealing with phishing scams.
Also a big thanks to Alex @ItsArtBabes for the awesome animation at the top of this blog.
New blog posts every Wednesday and Sunday.
M.













